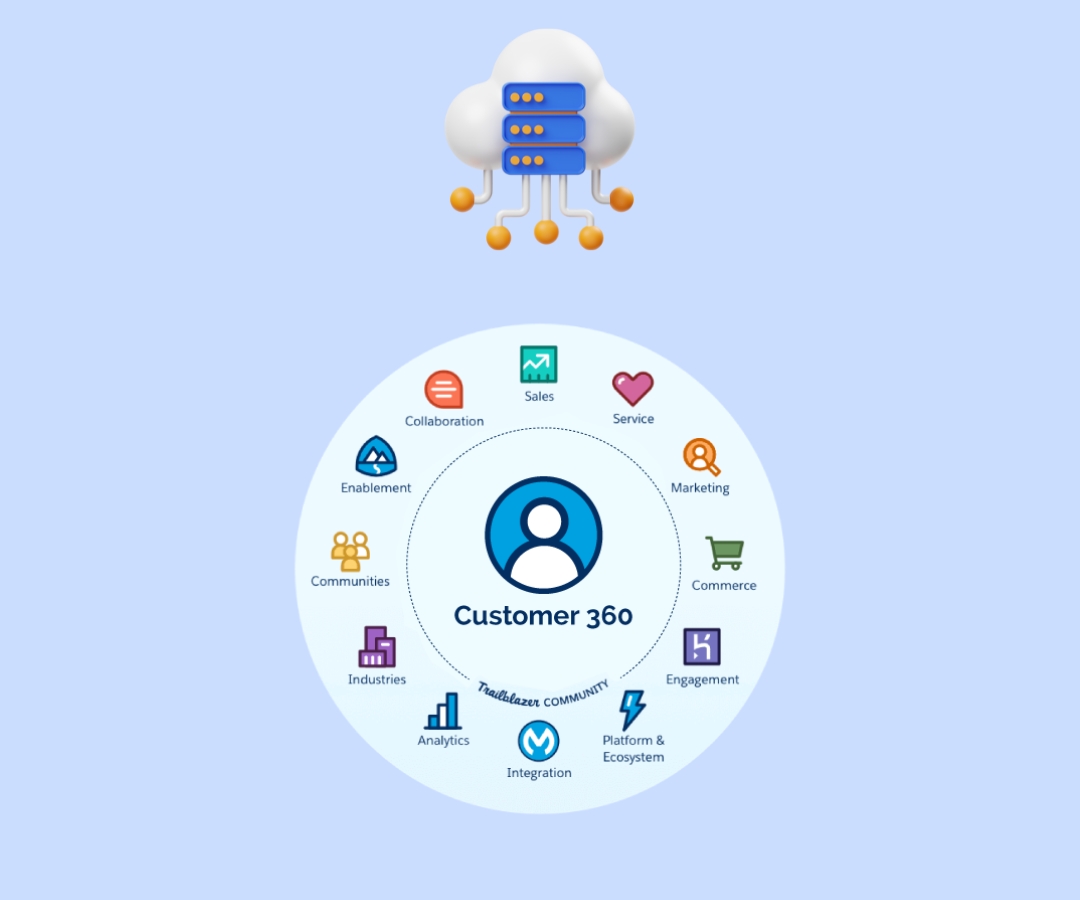
Customer 360 Platform has gained traction across the Salesforce ecosystem as a practical way to unify how teams access and use customer data. It promises better alignment between departments, faster insights, and a cleaner operational workflow. For many organizations, it opens the door to solving problems that have long existed in silos: mismatched records, fragmented support experiences, and inconsistent communication.
But to make that happen, organizations need more than tools. They need clarity, structure, and the ability to align their systems and teams around shared priorities.
Let’s dive into what Customer 360 looks like beyond the surface—how it works in real implementations, the challenges it brings, and what we’ve learned from putting it into practice.

What Customer 360 Is (and Isn’t)
Customer 360 isn’t a single product. Instead, it’s an approach to connecting Salesforce’s various clouds—Sales, Service, Marketing, Commerce, and more, around a unified customer profile.
This unified view is made possible through:
- Shared identity management (Customer 360 ID)
- Integrated data platforms, including Salesforce Data Cloud
- APIs and event frameworks for data synchronization
The goal is to allow teams to work from the same set of data, no matter what system they’re in. But to get there, you need to actively manage data consistency, resolve identity mismatches and connect platforms in a thoughtful, organized way. In practice, Data Cloud not only centralizes your data but also unlocks analytics, segmentation and AI-powered insights across every Salesforce Cloud.
What Happens When You Go Live
Once you start building out Customer 360 in production, several common realities set in:
1. Identity Resolution Takes Work
It’s rare for companies to have clean, consistent customer records across all systems. Different platforms may store different fields, use different naming conventions, or have duplicated data.
Building unified profiles often involves:
- Matching and merging customer records
- Standardizing key fields like names and email addresses
- Creating rules for which systems are the source of truth
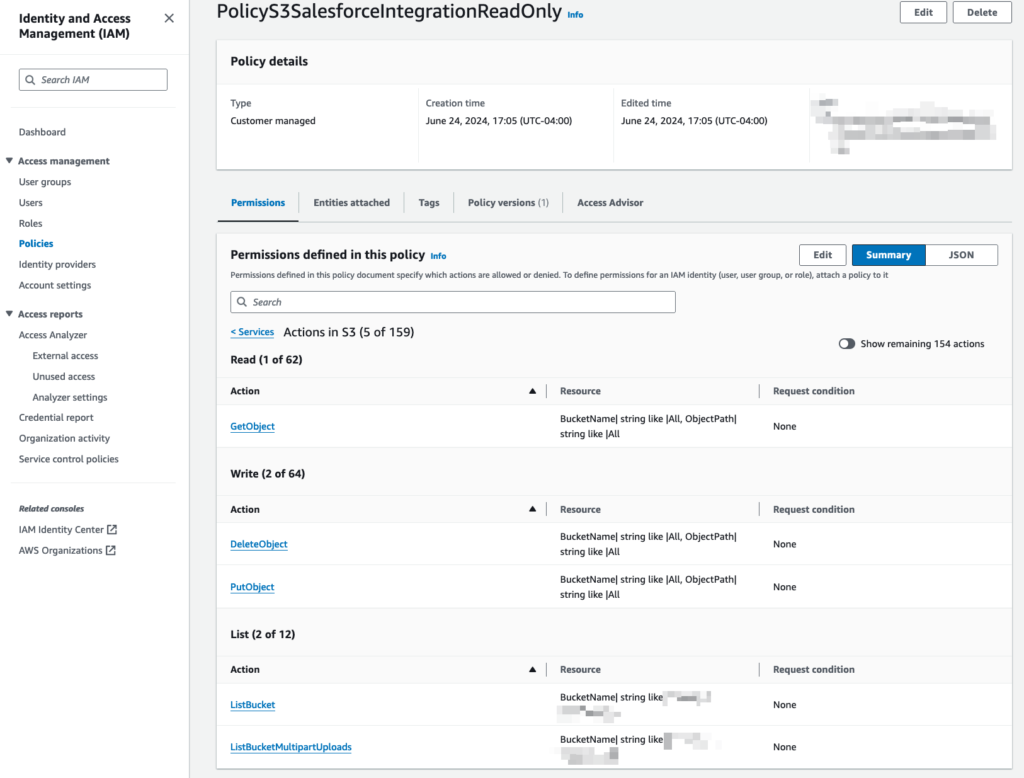
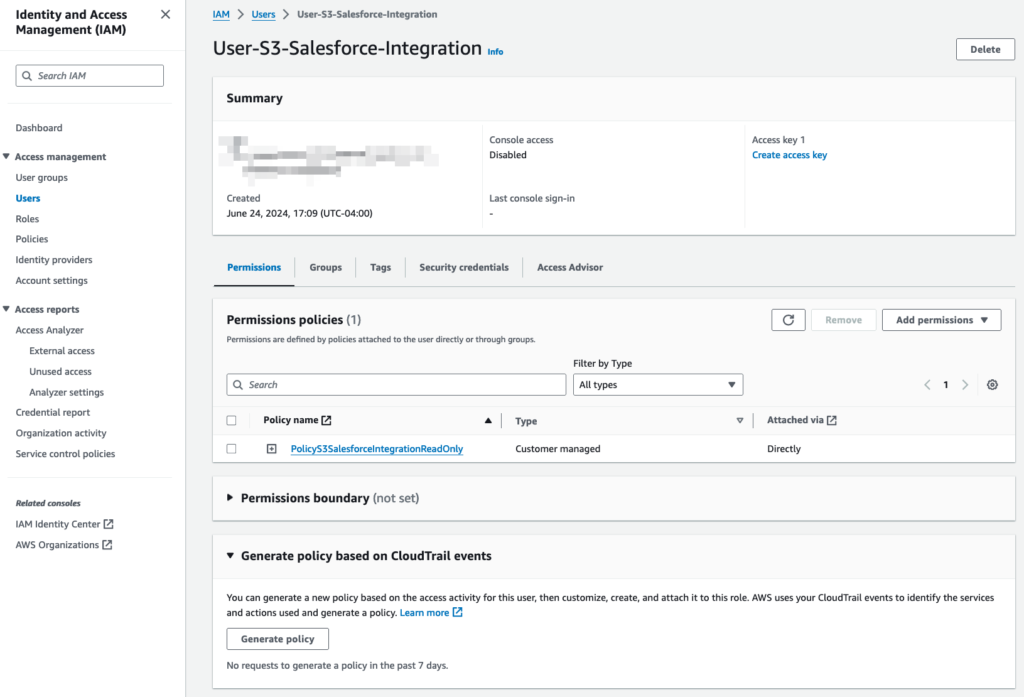
At Oktana, we often help organizations use Salesforce Data Cloud, MuleSoft, or even custom logic in Apex to bring these records together.
2. Real-Time Feels More Like Near-Time
Although Customer 360 aims to support real-time experiences, most integrations operate on slight delays. For example:
- APIs may introduce several seconds of latency
- Downstream systems may batch data updates
- Event-driven architectures depend on the speed of subscribers
For teams using Customer 360 to personalize experiences or power support workflows, it’s important to set the right expectations about what’s actually happening live and where there may be a slight delay.
3. Data Governance Becomes a Priority
Bringing together multiple systems means agreeing on rules around who can access, update, or override certain information.
A successful Customer 360 setup usually includes:
- Role-based access control
- Clear data ownership policies
- Logging and change tracking
- Compliance support (GDPR, HIPAA, etc.)
These features don’t appear automatically, they need to be defined and implemented as part of your system design.
4. Cross-Cloud Connections Require Custom Solutions
While the Salesforce ecosystem is increasingly connected, Sales Cloud doesn’t automatically inform Marketing Cloud, and Service Cloud doesn’t always update Commerce Cloud. Making those connections work depends on your use cases.
For example:
- A new support case might need to pause a marketing campaign
- A returned order might need to update a customer profile in Service Cloud
These actions require integration work. At Oktana, we often build custom solutions using Platform Events, External Services, or integrations via MuleSoft.
Tips Before You Start
Here are a few key steps we suggest before launching any Customer 360 effort:
Audit Your Data
- Where does customer data live today?
- Are there duplicates or conflicts between systems?
Define Use Cases Early
- Are you improving support response time?
- Creating better marketing segments?
- Reducing order errors?
Roll Out in Phases
- Start with a small, meaningful use case
- Add complexity as you gain clarity and internal momentum
Make Time for Identity Work
- Profile resolution takes longer than expected
- Plan for testing, feedback, and refinement
Work with Teams Who’ve Done It
- Experience helps avoid dead ends and rework
How Oktana Helps Teams Build with Customer 360
We’ve spent over a decade building custom Salesforce solutions, from core CRM setups to connected apps across Marketing Cloud, Commerce Cloud, and more. Our Customer 360 work builds on that foundation.
Our approach includes:
- Designing data models that fit your business, not just the tools
- Building integrations using MuleSoft, Platform Events, and Apex
- Setting up dashboards and analytics in Tableau or Salesforce reports
- Supporting adoption through user training and technical documentation
We also understand that every organization has different systems, goals, and constraints. That’s why we don’t approach Customer 360 with a one-size-fits-all mindset.
It’s a Platform, Not a Shortcut
Customer 360 offers real value, but it’s not a shortcut. It’s a framework for building a shared view of your customers across the organization. That requires careful planning, flexible architecture, and the right team to implement it.